Object-Level Security:
Using Object-level security we can prevent a user from viewing, creating, editing, or deleting any instance of a particular object type. We can specify object permissions in permission sets and profiles. Permission sets and profiles are collections of settings and permissions that determine what a user can do in the application.
Field-Level Security:
Using field-level security we can allow user to have access to an object while limiting their access to individual fields in that object. Using field-level security we can control whether a user can view, edit, and delete the value for a particular field on an object. Permission sets and profiles are collections of settings and permissions that determine what a user can do in the application.
Record-Level Security:
We can also control access settings for records.
To specify record-level security, we define organization-wide sharing settings, role hierarchy, and create sharing rules.
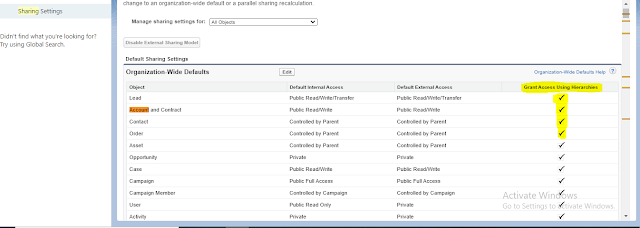
1) Organization-wide sharing settings:
For OWD refer article : What is OWD or Organization-Wide default in salesforce?
2) Role hierarchy:
Role hierarchy is a way to give wider access to a record.
If we define a role hierarchy and check Grant Access Using Hierarchies checkbox it ensures that users higher in the hierarchy can always access the same data as users who are lower, regardless of the organization-wide default settings.
- We cannot uncheck grant access using hierarchy for standard objects.
- If we uncheck grant access using hierarchy for the custom object than the user above the record owner will not be able to see record if OWD for an object is private.
- Although it’s easy to confuse permission sets and profiles with roles, they control two different things. Permission sets and profiles control a user’s object and field access permissions. Roles primarily control a user’s record-level access through role hierarchy and sharing rules.
hello sir kindly upload some tutorial on flow because your contents are awesome
ReplyDelete